อับเดดภาษาไทยสำหรับ Joomla 2.5.5
แพคเกจไฟล์ภาษาไทยสำหรับ Joomla 2.5.5 (ใช้ได้กับ Joomla 2.5.6) ออกมาแล้วครับ โดยชุดไฟล์ภาษาไทยนี้ ทางทีมจูมล่าลายไทย (JoomlaCorner) ภายใต้การสนับสนุนจากบริษัท มาร์เวลิค เอ็นจิ้น จำกัด สำหรับท่านที่ได้ติดตั้งภาษาไทยเวอร์ชั่น 2.5.4 ไว้แล้ว ระบบจะแจ้งเตือนว่าไฟล์ภาษามีการอัพเดด ท่านแค่ทำการคลิกเพื่ออัพเดดก็จะติดตั้งไฟล์ภาษาไทยชุดนี้ได้ทันที
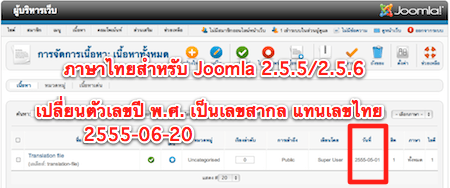
นอกจากนี้ในส่วนของระบบวันที่ จะถูกเปลี่ยนเป็น ปีพุทธศักราช โดยเปลี่ยนจากตัวเลขไทยเป็นเลขสากล แทน เช่น 20 มิถุนายน 2555 ในส่วนของคำแปลนั้น ยังมีอีกหลายส่วนที่ยังไม่ได้แปล หากสมาชิกท่านไทยสนใจจะอาสาช่วยกันแปลแล้วส่งกลับมาให้ทีมงาน ก็จะเป็นประโยชน์กับเพื่อนๆ อีกจำนวนมากครับ ลำพังทีมจูมล่าลายไทย เองมีงานในส่วนอื่นๆ ที่ต้องทำร่วมกับทีมพัฒนาจูมล่าอีกมาก เพื่อพัฒนาออกมาแจกจ่ายให้ทุกท่านได้ใช้งานกัน
คลิกที่นี่ เพื่อดาวน์โหลดไฟล์ภาษาไทย สำหรับ Joomla 2.5.5 v.1
 ทีม Joomla! Project ได้ปล่อย Joomla 2.5.6 ออกมาให้ได้ใช้งานเป็นการเร่งด่วน รุ่นนี้แก้ไขปัญหามีความสำคัญสูงหลายจุดในรุ่น 2.5.5 ที่เพิ่งออกไป เป้าหมายที่ยิ่งใหญ่ของทีมผ่ายผลิต คือการให้ความช่วยเหลือต่อไปอย่างสม่ำเสมอ เพื่อชุมชน Joomla. ท่านสามารถเรียนรู้เพิ่มเติมเกี่ยวกับ Joomla! Developement ที่
ทีม Joomla! Project ได้ปล่อย Joomla 2.5.6 ออกมาให้ได้ใช้งานเป็นการเร่งด่วน รุ่นนี้แก้ไขปัญหามีความสำคัญสูงหลายจุดในรุ่น 2.5.5 ที่เพิ่งออกไป เป้าหมายที่ยิ่งใหญ่ของทีมผ่ายผลิต คือการให้ความช่วยเหลือต่อไปอย่างสม่ำเสมอ เพื่อชุมชน Joomla. ท่านสามารถเรียนรู้เพิ่มเติมเกี่ยวกับ Joomla! Developement ที่


